 Accessing Databases Behind a Firewall
Accessing Databases Behind a Firewall 
To protect your database, it is usually located on a database computer behind a firewall, for example within your company's LAN (local area network). To connect to your database, clients from outside the firewall connect to the global listener and then an installation-specific X server (SAP MaxDB communication server) on the database computer behind the firewall, or directly to an installation-specific X server.
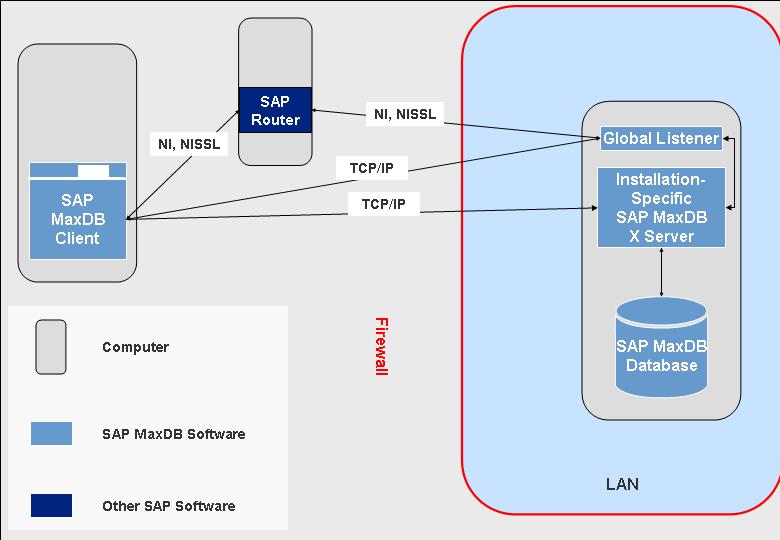
Example: Accessing SAP MaxDB Databases Behind a Firewall
Procedure
To enable access for client programs, proceed as follows:
Open the following ports in your firewall:
All ports of the global listener
TCP/IP port of the X server of the installation to which your database belongs
Ports and Protocols of the SAP MaxDB X Servers Scope
Default Port
Function of the X Server
Protocol
Protocol Identifier
All installations on the database computer
7210
Global listener
TCP/IP
remote://
7269
Global listener with SAP network protocol NI (for connections via SAPRouter, only available in SAP systems)
NI
(based on TCP/IP)
sapni://
7270
Global listener with SAP network protocol NI and SAP encryption library (for connections via SAPRouter, only available in SAP systems)
SSL/TLS
NISSL
(based on TCP/IP)
remotes://
sapnis://
First installation <installation_1> on the database computer
7200
X server for <installation_1>
TCP/IP
remote://
Second installation <installation_2> on the database computer
7203
X server for <installation_2>
TCP/IP
remote://
Separate Database Studio installation
7299
X server for the separate Database Studio installation, only used by the system to access the local user management database .UMDB
TCP/IP
remote://
For more information about opening ports, see your firewall documentation.
Restrict access to these ports to those computers that need to access the database.
More Information
Concepts of the Database System, Network Communication
Documentation about SAProuter is available in the SAP Library at http://help.sap.com.